AIM

The Challenge of Migrating Healthcare Applications to the Cloud
Explore the decisions that must be made within the healthcare sector when it comes to migrating applications...

Segmentation That Isn't Hard
Segmentation is a concept that has been around as long as we've been connecting networks. It is a proven...

Automated Endpoint Incident Response: An Enterprise Guide
Strong cybersecurity has always been an essential component of a company's digital transformation success....

How to Tackle Ransomware by Managing Human Risk
CybSafe's analysis of ICO data finds the number of incidents of ransomware reported has doubled in a...

Innovating in the Exponential Economy: Chapter 2
For all businesses, innovation is crucial for competitiveness and survival but it is notoriously hard...

Protect your organization from ransomware
Get a glimpse of the criminal players who operate within the underground ransomware economy. We'll help...

The Definitive Guide to Sharepoint Migration Planning
If I've learned anything in more than a decade of working with SharePoint, it's that migration is more...

2021 State of Malware Report
The story of 2020 is of the devastating COVID-19 pandemic, and of how the world adapted. The story of...

Zero-trust Solutions for Comprehensive Visibility and Control
Zero-trust solutions exist for nearly every part of the network. However, a piecemeal approach can leave...

How to Help Prevent Increasingly Rampant Brand Exploitation
Brands have been the unwitting victims of scams since time immemorial. Now, in the age of phishing, it's...
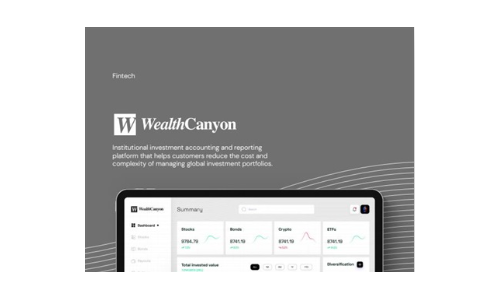
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...

ERP Modernization Is Business Transformation
Learn how a cloud-based ERP system can help your organization get better business insights, increase...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

