Applications
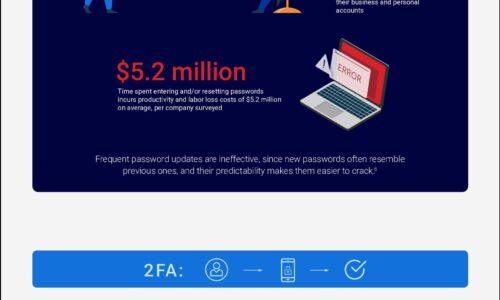
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Innovating in the Exponential Economy: Chapter 2
For all businesses, innovation is crucial for competitiveness and survival but it is notoriously hard...

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

The top 3 IT pains of the new reality and how to solve them
For those considering a better ITSM solution, there are powerful reasons to think beyond just that singular...

NAIKON: Traces from a Military Cyber-Espionage Operation
NAIKON is a threat actor that has been active for more than a decade. The group focuses on high profile...

Getting More from Less
IT and security professionals know that the threat landscape is dynamic. Every day, attackers are getting...

Internal Firewalls for Dummies Guide
Organizations can no longer rely on edge firewalls alone to provide network security. Once attackers...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






