Applications

The Role of Immutable Storage in Ransomware Protection and Recovery
All organizations need to face an unpleasant truth: It is not a question of 'If' they will experience...

Next-Generation Anti-Malware Testing For Dummies
How did you choose your anti-malware solution? Did you put it through the same rigorous process as your...
Would you be ready ....if your employees want to work from Mars?
Midsize companies play a key role in the global economy, driving a large share of job creation, economic...

Meraki for Financial Services: Secure Branch of the Future
The future of finance is digital. Do you have the agility to embrace the opportunity? The financial world...
Empowering Developers Through Cloud Services
The enterprise is under tremendous pressure when it comes to modern application deployment. The industry...

Overcoming the Top Five Gaps in Office 365 Data Protection
Microsoft Office 365 is widely used. Whilst it does offer a variety of system availability and data protection...

How financial firms use Box to build stellar experiences
From ordering takeout on an app to joining video calls, the way your customers work and play is constantly...

The CIO's Guide to Data and Analytics Innovation
Discover how Workday enables businesses to make faster, better decisions with one source for all your...
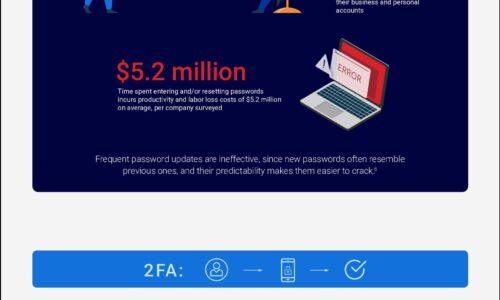
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




