BYOD

The definitive guide to Citrix Workspace
User experience and productivity. Use this guide to understand why Citrix Workspace delivers the solution...

Getting Started with Advanced Analytics
This planning guide provides valuable information and practical steps for IT managers who want to plan...

The growing role of web browsers to support Cloud Workers
Forrester Research studied how technology is changing as workers spend more time in the cloud. The Cloud...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...

Don't pay the ransom
In simple terms, ransomware is malicious software that either encrypts your data or otherwise stops you...

Meraki for Financial Services: Secure Branch of the Future
The future of finance is digital. Do you have the agility to embrace the opportunity? The financial world...

Beyond the Cubicle: Life in the Digital Workspace
These days, rarely is the modern workplace a static location where employees go everyday to be productive....

Moving Forward in a Work-from- Anywhere World
Welcome to The Gorilla Guide To…® Moving Forward in a Work-from-Anywhere World, Foundation Edition....

4 Low-Code Best Practices for SAP Fiori Apps
It has been proven that enterprise IT teams that include a no-code/low-code approach for their SAP app...

Slack is Custom-Built for Enterprise Companies
Over the past few weeks, we've all been challenged to rethink how our teams work together. We've had...

State of the Phish 2019 Report
What did the phishing landscape look like in 2018? Is general end-user awareness of phishing and other...

Data In, Value Out
In today's increasingly data-driven business landscape, the companies who succeed are typically those...
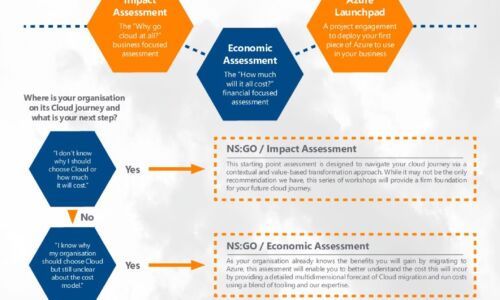
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
