Cloud Applications

Workday Enterprise Management Cloud Platform: The Power to Adapt
With market changes, global disruptions, competitive pressures, and rapid innovations in technology,...

Four Reasons Your Content Is More Secure in the Cloud
Why You Should Migrate Now. In IDG's new ebook, 4 Reasons Your Content is More Secure in the Cloud, you'll...

How to secure your business with the Content Cloud
Hope is NOT a strategy: Secure your business with the Content Cloud Seems like every week there's news...

Avoiding Cloud Data Cost Overruns
The anticipated benefits of cloud computing have encouraged organizations to accelerate adoption of cloud-based...

A More Effective CIO-CFO Partnership
How are IT leaders achieving success in a changing world? To find out, Deloitte and Workday surveyed...

2020 CIO Cloud Data Management Initiatives
According to the results of Frost and Sullivan's Digital Transformation survey, 99% of businesses are...

Making the Move to Cloud-Based Archiving: A Step-by-Step Guide
Our digital world is generating a massive explosion of data coming from multiple communication channels....

IT's 5 Toughest Work from Home Challenges
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...
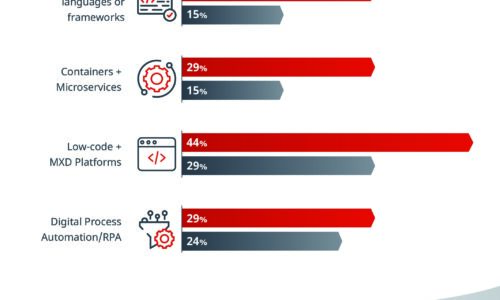
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

File Services with Azure NetApp Files and Cloud Volumes Service
NetApp Cloud Volumes Service and Azure NetApp Files offer something brand new: a fully-managed service...

Sotero Data-In-Use Encryption
Though encryption is the most effective way to reduce the probability of a security breach, traditional...

Speed Up Your Digital Transformation With The Cloud
In this Content Services in the Cloud Guide by AIIM, we explore how companies are tackling critical document...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

