Cloud Computing
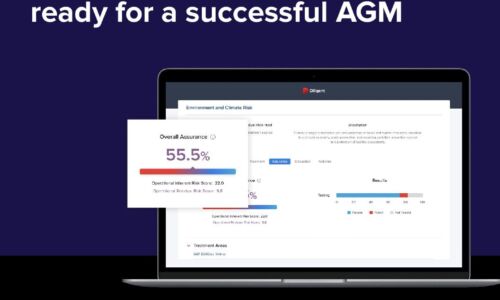
4 tips to ensure your board is ready for a successful AGM
The 2022 AGM season is on course to see unprecedented levels of challenge for boards and businesses....

The Anatomy of an Insider Threat Investigation: A Visual Guide
For decades, perimeter-based security strategies have been the starting point for most cybersecurity...

What you need to know about upcoming ESG regulations
New ESG regulations are being proposed across the world. But ESG is about more than just meeting requirements....

Stuck in the waiting room
Recent changes in the business world have challenged our assumptions about where employees work, how...

How media companies thrive in the digital age
As technology and media continue to evolve at a rapid pace, publishers, producers, editors, and filmmakers...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Avoiding Cloud Data Cost Overruns
The anticipated benefits of cloud computing have encouraged organizations to accelerate adoption of cloud-based...

Reinventing work - New imperatives for the future of working
Following one of the most challenging years in business history, the pandemic has forced every company...
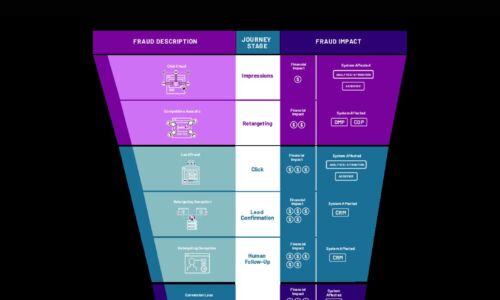
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

10 Endpoint Security Problems and How to Solve Them
Companies are facing massive cybersecurity challenges – many of which are rooted in the endpoint. In...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



