Cloud Computing

Raising the Bar for Web Application and API Security Solutions
Securing the web applications and APIs that underpin cloud architectures is a challenge for security...

How chemical companies can achieve a new level of enterprise performance
Mastering the challenges of an ever-evolving enterprise has always been a fundamental part of the day-to-day...

How to Secure Multicloud
The promise of cost savings, flexibility, and agility is making it easier for more organizations to embrace...

Forrester Wave, We’re a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

How To Maximize Protection and Access, On Campus Or Off
Colleges and universities are increasingly dependent on cloudbased apps and mobile connectivity. Meanwhile,...

University of Surrey's Edification for its Cyber Protection
The University of Surrey is a public research university in Guildford, England, receiving its royal charter...
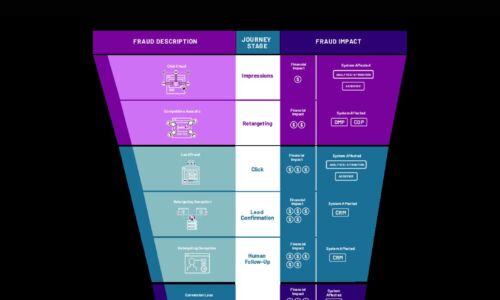
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

What Every Distributed Workforce Needs
Adopt a digital-first strategy for your distributed workforce To help your 'anywhere organization' succeed,...

5 Reasons to Upgrade Your Symantec Email to Proofpoint
Symantec is now part of Broadcom, a semiconductor manufacturing company. For Symantec customers of all...

Balancing Business Continuity with Innovation
Organisations can still remain innovative during times of crisis. With Workday, you can lead your organisation...

Privilege Access Management Buyers' Guide
Security breaches show no signs of slowing, and credential theft is the number one attack vector. Privileged...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


