Compliance

What Today's Retailers Need in a Security Architecture
Retail cybersecurity in the age of the omnichannel customer experience requires CIOs and vice presidents...

Transform your business with machine learning
8 stories of machine learning success By providing the broadest and most complete set of machine learning...

The Need for Speed: Second Generation EDR
Endpoint security plays an integral role in modern security architecture. While initially focused on...

Merger and Acquisition IT Integration: Active Directory
Each IT integration project is unique based on the timelines, the makeup of the environment and the goals...

Dell Technologies Continuously Modern Storage eBook
In a modern, data-driven economy, business success—or conversely, business struggles—often equate...

2021 Buyer's Guide to Comprehensive Cloud Security
Cyber resilience comes when you've secured your multi-cloud infrastructure and enabled your DevSecOps...

Workday for the Hospitality Industry
With change the only constant today, hospitality leaders need a better way to accelerate digital transformation...

Enterprise Cloud Solutions
Many traditional infrastructure vendors would have you believe that hyperconverged infrastructure is...

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

For digital sovereignty and transparency in the cloud
Shared use of infrastructure not only saves resources but also enables companies to push ahead with digitalisation...
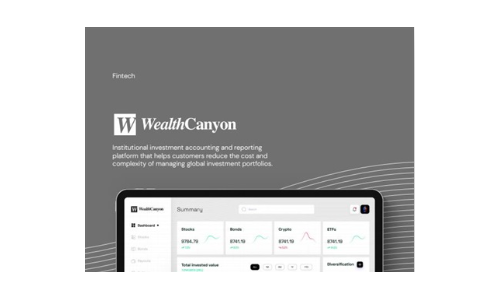
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...

Stop hopping on one leg
Go from velocity to value with dynamic DevOps. Don't let old systems and manual processes hobble your...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

