Data Centers

An Overview of Cato Data Loss Prevention (DLP)
ata is the most valuable asset a modern enterprise has. The evolving threat landscape and shift to cloud...
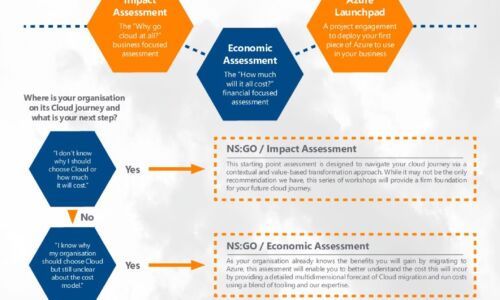
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

CISO's Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

Navigating the Cloud: Key factors for long term success
The cloud is not only here to stay, its impact is growing. As cloud-based solutions and capabilities...

Long-Term Data Retention with Veritas NetBackup
This white paper provides a technical overview of cloud storage as a long-term retention storage solution...

Digital acceleration in the time of coronavirus
Business decision-makers around the world were collectively blindsided by the scale and speed that working...

Accelerate Your Cloud Journey with an Intelligent Data Catalog
There's a generational shift happening in data management. On-premises databases and data warehouses...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






