Data Recovery
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Untangling the Web of Cloud Security Threats
Changing technologies and evolving threats make IT security more challenging. Business units are adopting...

The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...

Best Practice Makes Perfect: Malware Response in The New Normal
Before Covid-19, cyber security teams already confessed to being overworked – as high-profile security...

3 Ways to Reduce the Risk of Data Loss
Amid the fast-moving digital landscape, security risks are on the rise. People, devices, and objects...

The Gorilla Guide to Rapid Restores with Flash and Cloud
Welcome to this Gorilla Guide covering enterprise data protection, backup, and recovery. The purpose...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...
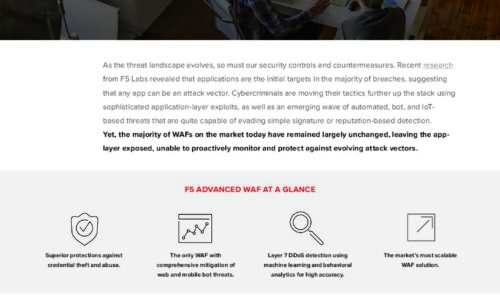
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

