Desktop/Laptop OS

Forrester: The Balanced Security Imperative
Balanced security requires firms to transition from treating privacy and data security as compliance...

14 Questions to Ask Your Application Security Vendor
When evaluating application security vendors, you have a great deal to consider. Understanding your goals...
Avoiding Container Vulnerabilities
Containers offer an unprecedented opportunity to scale cloud-based services, make incremental changes...

Security and risk management in the wake of the Log4j vulnerability
Security leaders agree: Log4j has irrevocably changed the risk landscape. Get a quick refresher on the...

Modern Blueprint to Insider Threat Management
Taking a People-Centric Approach to Your Insider Threat Management (ITM) Programme. Insider threats can...

Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...

Addressing the Top 10 Security Issues Organizations Face
Cybersecurity must be a top-level priority for any organization and for many it is. Security should be...

Oracle Cloud@Customer Brings Full Cloud Experience On-Premises
Oracle Autonomous Database on Exadata Cloud@Customer and Dedicated Region Cloud@Customer powered by 2nd...

CIO Roadmap to Hybrid and Multi-Cloud
While cloud has become a key driver of business expansion and operational efficiency, business and IT...
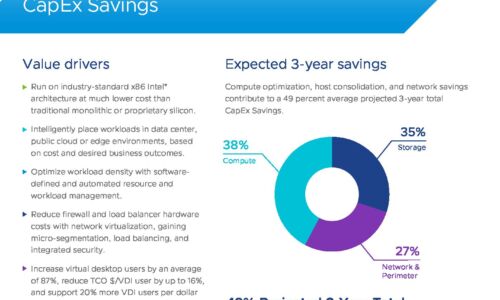
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

Supply Chain Security Is Tough: So What Should Good Look Like?
Managing and securing software supply chains end to end has been a challenge for organizations the world...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


