Desktop/Laptop OS

Cybersecurity: Prevention is better than the cure
Prevention is almost always better than the cure. But how many organisations are living up to the promise?...

What Today's Retailers Need in a Security Architecture
Retail cybersecurity in the age of the omnichannel customer experience requires CIOs and vice presidents...

Network Security that sets the standard for local government
When it comes to network security, organisations can — and must — learn from the experiences of others....

The Definitive Guide – Replace Google Analytics
This guide gives you the breakdown on warehouse-first analytics, why it's the trustworthy, efficient,...
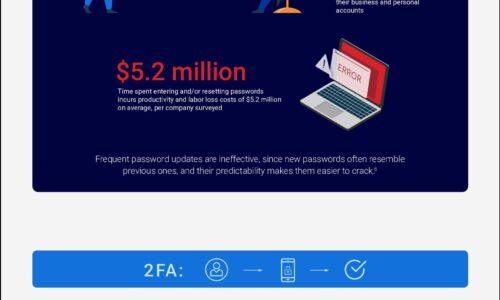
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Get Total Endpoint Security with KACE
As an IT professional, you're likely under pressure to manage an increasingly complex environment, while...

5 Steps to Battle Endpoint Cybercrime with KACE
Cyberattacks are increasing across all industries, and cybercriminals are savvier than ever. While the...

Digital Transformation & Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...

Moving Forward in a Work-from- Anywhere World
Welcome to The Gorilla Guide To…® Moving Forward in a Work-from-Anywhere World, Foundation Edition....

Modern infrastructure for better end user experiences
Many companies with existing EUC deployments are refreshing their technology stacks to deliver a better...

2022 Cloud Threat Report, Volume 3
Cybercriminals are racing to exploit vulnerabilities, and the scope and damage potential of their cyber...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


