Desktop/Laptop OS

Use Case - Optimizing SIEM
Security Information and Event Management (SIEM) solutions form the core of many organizations' security...

Selenium Grid Build vs. Buy
Automated testing is essential to software development teams that are moving to continuous integration...

Charting a Course to SAP Modernization Success
As enterprises plan their SAP modernization efforts, they are looking for solutions that allow them to...

What You Don't Know Can Hurt You: Expert advice on measuring risk
Managing risks begins with measuring risks. But how do you measure risks accurately? How do you share...

5 Ways Red Hat and AWS Help Modernize your SAP Landscape
Migrating to SAP S/4HANA® offers an opportunity to simplify your SAP landscape by moving to a hybrid...

Three reasons to manage Office 365 with Citrix Workspace
Are you considering migrating to Microsoft Office 365 or already facing challenges with the move? Don't...

Solve the security puzzle with end-to-end security solutions
As an IT decision maker, you're focused on finding effective solutions you can implement quickly and...
The Total Economic Impact™ Of Tanium
Tanium helps organizations secure and manage endpoints from a single platform. The Tanium platform starts...
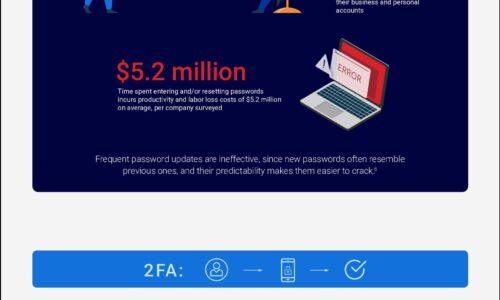
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

The Future Is Flexible: Six Areas to Make It Work.
Over 50% of businesses are preparing for long-term, flexible work patterns. But the rush to adopt remote...

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

Moor Insights: Cloud is Built on Modern Infrastructure
The modern enterprise lives in a multi-cloud world, where delivery of infrastructure resources and IT...

Winning in the New Era of Data Management
In the data-driven age, information is as valuable as currency. Entire industries are being disrupted...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
