Desktop/Laptop OS

Cybersecurity for retail: Prevention is better than the cure
Prevention is almost always better than the cure. But how many organisations are living up to the promise...

Automated Endpoint Incident Response: An Enterprise Guide
Strong cybersecurity has always been an essential component of a company's digital transformation success....

Building the foundation of a mature threat hunting program
Many organizations, especially large global enterprises, don't always have the best visibility into how...
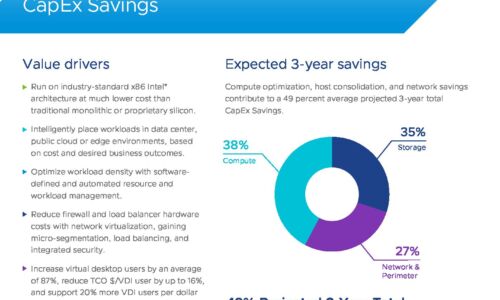
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

Prevent Ransomware From Cyber Disaster
Modern ransomware is one of the most significant cybersecurity threats to critical services, compute...

Going Digital For Business Continuity
COVID-19 has created a global reorientation in business operations. Global lockdowns have reprioritized...

Modernize the workforce experience
It's more than a concept, it's our approach to modernizing your workforce. Our products, solutions and...

The Business Value of Red Hat Enterprise Linux
Linux has firmly established itself as a preferred delivery vehicle for modern applications, in addition...

Deep Learning For Dummies
Take a deep dive into deep learning Deep learning provides the means for discerning patterns in the data...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




