DevOps

How Do Vulnerabilities Get Into Software?
There isn't a business today that doesn't produce or purchase applications in order to run more efficiently....

Fortinet Security Solutions for SAP S/4HANA
With today's challenges and economic climate, organizations leverage enterprise resource planning (ERP)...
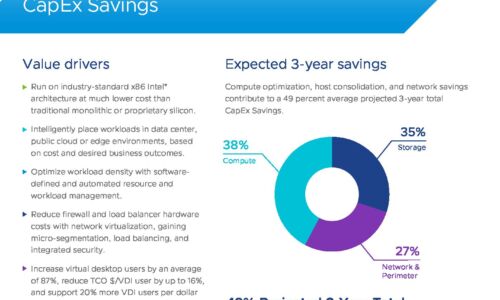
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

5-Step Buyers Guide to Multi-Cloud Management
Chart your roadmap to multi-cloud success by re-envisioning your approach to management on premises and...

Securing applications in the education industry
The role of technology in education has changed radically in the last two years. Like many other areas...

How to Test and Debug Your Mobile Apps in the Cloud
In a heavily fragmented mobile environment, developing applications, which are compatible with multiple...

8 Deployment Pattern Structures to Transform your CI/CD
Modernize your DevOps with the right deployment pattern Good deployment patterns mean fast and repeatable...

Business Value of Cloud Modernization
Explore the business value of proven modernization paths Understanding the business value of infrastructure...

Learning From The Low-code Playbook
Low-code development is proliferating worldwide — but a rift has opened between the early adopters...

Database Solutions Pocket Book
Given the fast pace of modern business, traditional enterprise infrastructure is ill-suited to meet the...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



