Endpoint Security
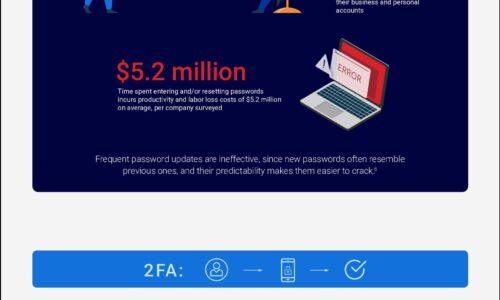
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Blackberry Guard: Solution Brief
While cloud and mobile technologies provide significant opportunities for digital transformation, they...

Ransomware Prevention Is Possible
Ransomware is a form of malware that encrypts files to prevent victims from accessing their systems and...

Isolated Castles: Incident Response in the New Work From Home Economy
Since the shift to work from home, there's been a paradigm shift in the IT and security industry. The...

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

Escape the Ransomware Maze
Ransomware is an ever-evolving form of malware designed to steal business-critical data and then sell...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

The Promise of XDR for Effective Threat Detection and Response
In October 2020, the Enterprise Strategy Group (ESG), completed a research survey of 388 cybersecurity...

Optimizing Workload Placement in Your Hybrid Cloud
Many IT organizations are in the process of modernizing their infrastructure, as part of either a digital...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

The State of Email Security 2020
Global business is interspersed with a diversity of industrial sectors, united by a single, common communication...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


