Endpoint Security

Cloud Workload Protection
The hybrid cloud is at the centerpiece of digital transformation. Today, more than 90 percent of enterprises...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Consolidate Cybersecurity Vendors to Accelerate Detection and Response
Organizations of all shapes and sizes are increasingly embracing digital transformation, cloud-delivered...

How Intrinsic Security Protects Against Business Disruption
When it comes to IT, disruption is just another day at the office. From fending off cyberattacks to incorporating...

Ransomware Case Studies
Ransomware is a simple name for a complex collection of security threats. Attacks can be short and brutal,...

The Case for Secure Communications
The tapping of voice communications has occurred virtually as long as electronic communication has been...

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

Cybersecurity for retail: Prevention is better than the cure
Prevention is almost always better than the cure. But how many organisations are living up to the promise...

State of Ransomware: Invest now or pay later
Ransomware attacks continue at a blistering pace because organizations remain vulnerable to the exploits...

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

A CIO’s Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

Solve the security puzzle with end-to-end security solutions
As an IT decision maker, you're focused on finding effective solutions you can implement quickly and...
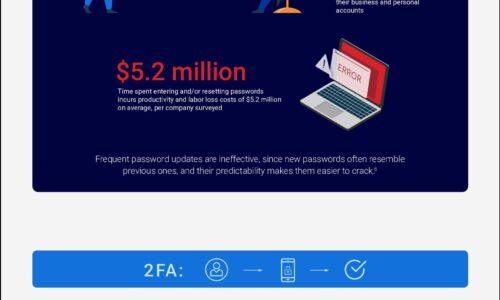
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
