ERP

Silver Linings: Licensing in the Cloud
When you hear the term 'Cloud Licensing', what do you think of? This simple term sounds rather innocuous...

CDP Beyond Marketing
Speed. Quality. Low cost. There used to be a saying that you could only have any two at the same time....

Ransomware Protection with Veritas NetBackup Appliances
Download this whitepaper to discover how to protect your backup and recovery infrastructure from attacks....

Parivartana - The Role of Data and Analytics in Social Transformation
From personalized healthcare to digital farming, and from energy management to digital governance solutions,...

Powering your organisation with an agile productivity stack
I wonder where our important files have run off to today.' When you've got one seamless, secure platform...

4 steps to automate and connect your organization
Every organization should be able to connect any system to ServiceNow to drive end-to-end process automation....

Redefining Modern Enterprise Storage for Mission-critical Workloads
The digital business demands being placed on enterprise-scale IT organizations are now so extreme that...
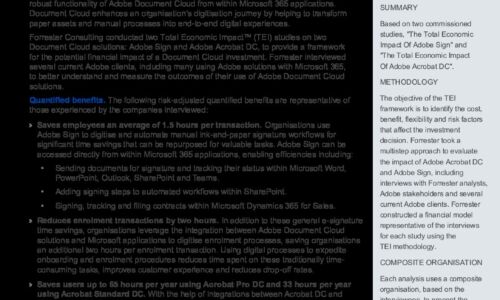
The Total Economic Impact of Adobe Document Cloud & Microsoft Spotlight
Forrester interviewed several current Adobe clients, including many using Adobe solutions with Microsoft...

Ransomware The True Cost to Business
Ransomware continues to dominate the threat landscape in 2022. Organizations are under siege from a wide...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




