Hardware

VMware Multi-Cloud Architecture: Enabling Choice and Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...
DDoS Attack Threat Landscape — Tracking DDoS Attack Trends in Q2'22
DDoS attacks are on the rise. Ransom attacks reached an all-time high in June 2022, the Ukraine-Russia...

Manufacturers get industrial strength security with private 5G.
5G technology has quickly evolved from aspirational to businessready, and many organizations are already...

2 Steps to Achieve Endpoint Compliance with KACE® by Quest
Next to ongoing security issues, meeting compliance mandates is one of the biggest challenges IT professionals...
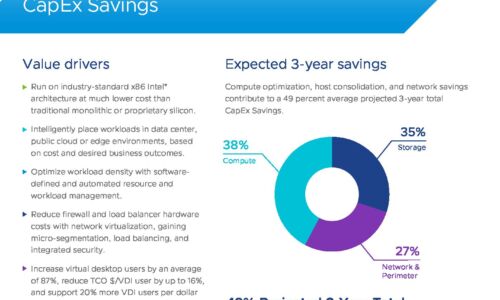
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

Understanding cybersecurity workforce problems and solutions in 2021
The findings in this large-format survey reinforce existing statistics and, in certain instances, actually...

Deploying Flexible Data Protection to Support Cloud Workload Placement
Digital transformation (DX) projects are designed to help organizations better utilize data for competitive...

Global Threat Landscape Report
Another half-year through unprecedented times has passed. But as unique as these times may feel, we continue...

Organizations Accelerating Their Digital Workplace Achieve Improvements
This study sought to understand whether, and to what degree, an organization's adoption of modern device...

Getting Started with Advanced Analytics
This planning guide provides valuable information and practical steps for IT managers who want to plan...

Designing Hyper-Aware Industrial Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

Personalization powered by machine learning
Create relevant, personalized customer experiences with machine learning Personalizing content for online...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
