Infrastructure Management
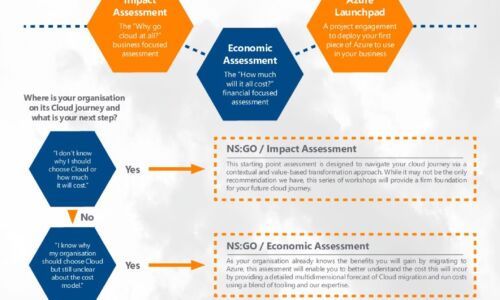
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Why Traditional EDR Is Not Working—and What to Do About It
If you work in infosec and haven't been living under a rock, you have undoubtedly heard of EDR. EDR,...

IoT Smart Cities & Buildings
Many of today's commercial buildings predate modern energy-saving tools and techniques. That means they...

Windows Virtual Desktop Jumpstart
Not all applications are web-based or designed to run from the cloud. Many applications still require...

Migrating Apps to the Cloud in 5 Steps
Cloud applications, platforms and services are changing the way enterprises compete for customers. The...

Data-Driven Transformation in Europe
Although governments across Europe may differ in their ideologies, statutes and constitution – there...

KuppingerCole Report: Privileged Access Management
Privileged Access Management (PAM) is one of the most important areas of risk management and security...

Designing Hyper-Aware Healthcare Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...

Strategies for successfully managing privileged accounts
Getting identity and access management (IAM) right for your standard users is hard enough. What about...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...

5 ways to reduce risk with continuous monitoring
The rise in breaches over the past few years has made it clear that many organizations are overwhelmed...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


