Internet of Things (IoT)

New Perspectives on Mobile Device Testing at a Global Scale
The old days of just translating the language in your app to make it readable to people in other countries...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

Blurred Lines and Blind Spots Report
Of the many effects the COVID-19 pandemic has had on business, one of the most dramatic has been the...

How to chose a managed extended detection and response solution
Managed Detection and Response (MDR) solutions are specialized security services that allow an organization...

What Makes Real Threat Intelligence
First popularized in terminology several years ago, threat intelligence means many things to many people....
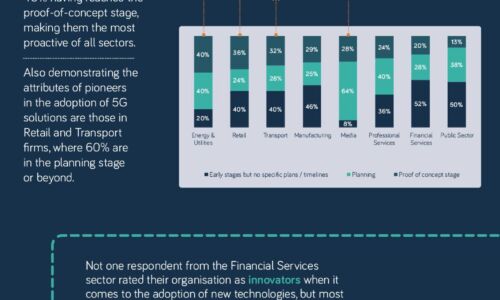
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Securing high tech industry network data
We all understand the negative impact of data loss, so why is it that so many organisations seem to be...

Unified Fast File and Object (UFFO) Storage
In this book, you get an idea of the vast potential for unstructured data — and also the infrastructure...

5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

How to Tackle Ransomware by Managing Human Risk
CybSafe's analysis of ICO data finds the number of incidents of ransomware reported has doubled in a...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



