IOT

The Perfect Storm: Why MDR is Your Only Option in Modern Cybersecurity
Covid, work from home, and bring-your-own-device have expanded our threat envelopes 1000X. Attacks with...

Identity Security: An Essential Piece of Your Zero Trust Strategy
Zero Trust is a security framework that aims to enable an organization's digital business while ensuring...

The top 3 IT pains of the new reality and how to solve them
For those considering a better ITSM solution, there are powerful reasons to think beyond just that singular...

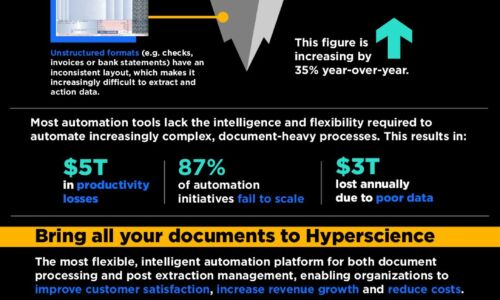
Reduce data processing time by up to 50%
As the world around us becomes more digitised, data is becoming more and more important. The problem?...

Automating Safety
As the overly-used phrase so correctly states: 'safety is no accident'. Dedication to safety-first culture...

DDoS Threat Landscape Report: DDoS Trends from Q3 2022
DDoS attacks are growing larger, stronger, and more sophisticated. In Q3'22, we observed a resurgence...

Understanding Log Analytics at Scale
The humble machine log has been with us for many technology generations. The data that makes up these...

Sustainable by Design
Manufacturers need to act on Sustainability and the best time is now! Read now to discover about securing...

Future-proofing endpoint management
New devices, platforms, applications, and technologies connecting to the network are overwhelming IT's...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.