IT Security

The Definitive Guide To SASE
What is Secure Access Service Edge (SASE) and why do you need it? Download the new guide to learn how...

Risk-Aware Data Privacy
Organizations around the world are scrambling to address data-privacy challenges amid workplace shifts,...

Identity Security: An Essential Piece of Your Zero Trust Strategy
Zero Trust is a security framework that aims to enable an organization's digital business while ensuring...

Better Security. Fewer Resources.
When you consider the number of headlines that appear on a regular basis about major data breaches —...
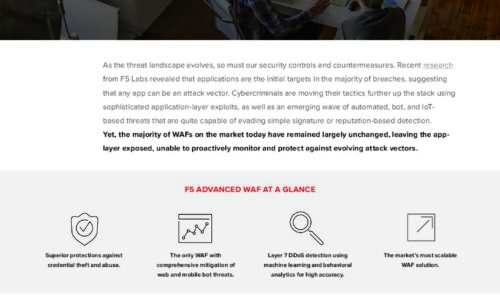
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

An Overview of Cato Data Loss Prevention (DLP)
ata is the most valuable asset a modern enterprise has. The evolving threat landscape and shift to cloud...

Box and ECM: Key integrations that drive digital transformation
Legacy ECM solutions simply can't keep up with the way you work today. Work is more mobile, more collaborative,...

Securing DNS by Design
3 Critical Protections from Your DNS Service: How Your Service Provider Can Protect Your Enterprise DNS...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...

10 Endpoint Security Problems and How to Solve Them
Companies are facing massive cybersecurity challenges – many of which are rooted in the endpoint. In...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



