IT Security

How to chose a managed extended detection and response solution
Managed Detection and Response (MDR) solutions are specialized security services that allow an organization...

Cyber Attack Trends: Check Point’s 2022 Mid-Year Report
The war in Ukraine has dominated the headlines in the first half of 2022 and we can only hope that it...

The State Of Email Security Report 2019
As cybercriminals continue to use email as a primary vehicle to steal data and deliver advanced threats,...

Solve the security puzzle with end-to-end security solutions
As an IT decision maker, you're focused on finding effective solutions you can implement quickly and...

The UK 2020 Databerg Report Revisited Executive Summary
Cloud technology hasn't been around for long, but it's evolution in that time has been nothing less than...

Enhancing Teams with enterprise-grade telephony
Today's businesses depend on a robust communications experience to drive innovation, and phone calls...

Maintaining ‘Business As Usual’ In Unusual Circumstances
The phrase 'business as usual' has a reassuring quality. It represents an ideal state in which the company...

All-Flash Buyer's Guide: Tips For Evaluating Solid State Arrays
Are you looking to switch to all-flash storage? Learn how to evaluate your storage options to increase...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

Respond and Evolve with Your Multi-Cloud
In a world of uncertainty, organizations on traditional IT platforms need something they can rely on...

The State of Email Security 2020
Global business is interspersed with a diversity of industrial sectors, united by a single, common communication...
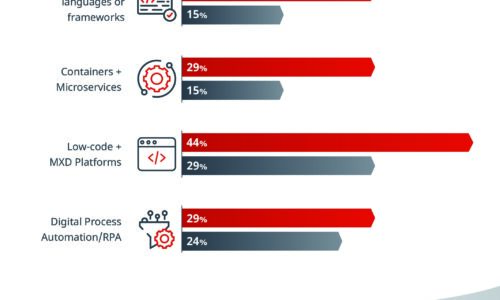
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

