Mobile Computing

Unlocking the Secrets of the Hybrid Cloud Leaders
For years, companies have been investing in new technologies, cultivating their culture, and transforming...

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...

VMware Multi-Cloud Architecture - Enabling Choice & Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...
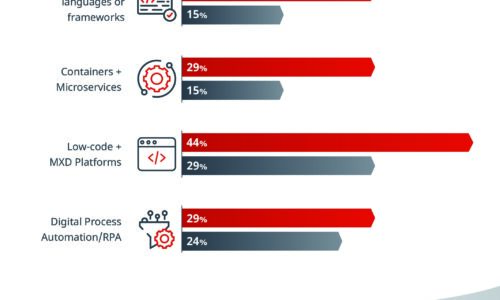
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Is your SaaS company's billing problem actually a data problem?
Planning a billing platform upgrade? Usage Engine, our purpose-built usage data management software,...

From Legacy Infrastructure to the Cloud: A Migration Journey in 5 Steps
Simplify your bank's move to the cloud It takes 8 hours to recreate a lost file, according to TechTarget....

Modern Blueprint to Insider Threat Management
Taking a People-Centric Approach to Your Insider Threat Management (ITM) Programme. Insider threats can...

Low-Code Guide
Low-Code development is the way to build apps more quickly by reducing the need to code. But that's not...

Reinventing work in development teams
Software engineering teams were often among the best placed to adjust to 2020's shift to working from...

The data challenges in usage-based subscriptions
The boldest companies are taking note and giving their customers the usage-based pricing they want. And...

Future Ready with SaaS Management Guide
For today's modern IT organizations, applications are driving both digital transformation and business...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

