Network Infrastructure

5 Critical Considerations for DDoS Mitigation
Distributed denial-of-service (DDoS) attacks remain one of the most effective methods used by cybercriminals...

Deliver secure, immersive gaming experiences with Cloudflare
Between growing their communities, meeting player expectations and defending against attacks, gaming...

Insider's Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

Threat Spotlight: Protecting your business in 2022
Cybersecurity threats are rapidly evolving. In the latest attacks, cybercriminals are using a range of...

Core connectivity: The key enabler of digital transformation
The phrase 'digital transformation' is a hot topic across industry right now. Based on the consultancy...
Accelerate your journey to microservices-based applications with Citrix ADC
Today, new application architectures like Devops microservices are opening great opportunities for innovation....

Common Browser Isolation challenges, and how to overcome them
A growing number of security teams are implementing a Zero Trust security strategy, in which no application,...

Aruba Unified Infrastructure
Network infrastructure and operations teams have never been more stretched. Hyper-distributed edge environments...
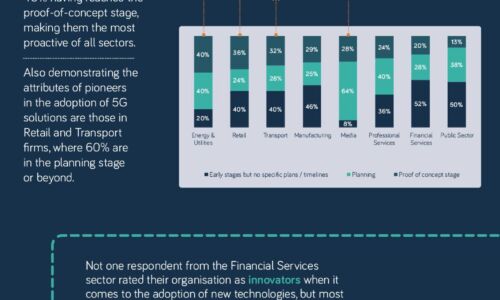
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...

Alphabet Soup: Making Sense of XDR, EDR, NDR, and SIEM
XDR, EDR, NDR, and SIEM. They are among the most prominent acronyms in cybersecurity. But what do they...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


