Open Source

Essential Operational Resilience
COVID-19's far-reaching impacts have thrashed many companies' Plan-A strategies, yet the pandemic offers...

5 Reasons to Prioritize Software Security
The pace of digital transformation has reached a speed never before seen, forcing organizations into...

Assessing Network Traffic Analysis (NTA) Requirements
Many organizations are struggling to detect, hunt, investigate, and respond to threats in an efficient...

Choosing a collaboration platform
Collaboration software can do so much more than simple messaging or conferencing. With the right platform,...

14 Questions to Ask Your Application Security Vendor
When evaluating application security vendors, you have a great deal to consider. Understanding your goals...

5 Usage data software options on the market
If you want to offer usage-based pricing to your customers, there are several IT solutions you can choose....

A Visual Landscape Of Cybersecurity
Our world has never moved faster in terms of cyber threats, security technology innovations and overall...

Advanced Application Threats Require and Advanced WAF
The threat landscape is dramatically different than it was just 5 years ago. A traditional web application...

Empowering Better Patient Care: Healthcare Mobile Solutions Hotsheet
The cost of healthcare is rising exponentially across the globe. Health services are challenged by a...

15 Ways Your Website is Under Attack
Web applications are the home of your business on the internet. The functionality within your website,...

Understanding Augmented and Virtual Reality
In the book, A Whole New Mind: Why Right-Brainers Will Rule the Future, author Daniel Pink describes...
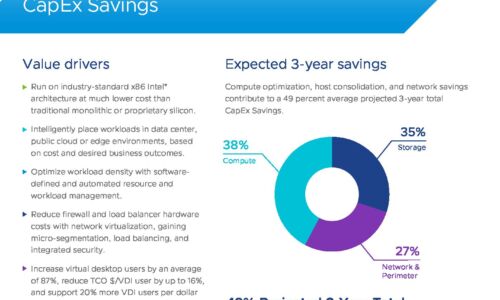
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

