Operating System

2022 MSP Threat Report
This report was created by the ConnectWise Cyber Research Unit (CRU)—a dedicated team of ConnectWise...

Security Starts Here - Privileged Access Management
The need to support safe and secure remote access for administrators, high-profile breaches (SolarWinds,...

Better Security. Fewer Resources.
When you consider the number of headlines that appear on a regular basis about major data breaches —...

Security and risk management in the wake of the Log4j vulnerability
Security leaders agree: Log4j has irrevocably changed the risk landscape. Get a quick refresher on the...
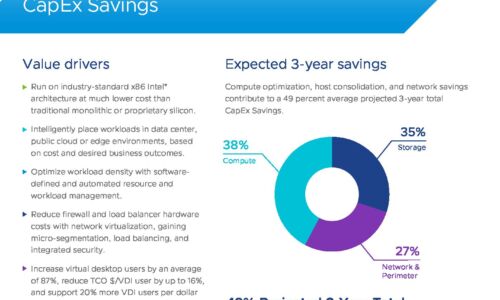
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

The Essential Guide to Preparing Your Network for the Cloud
How to meet your network requirements at every stop of your cloud transformation. In this eBook, we'll...

Infrastructure Monitoring 101
For any sized company, the rapidly expanding implementation of today's technology creates unique and...

Container Security 101: Understanding the basics of securing containers
Containers are quickly becoming an essential part of many IT development environments, but their popularity...

Sophos 2022 Threat Report
Interrelated threats target an interdependent world. We believe that shifting the timescale of attack...

Fortinet Security Solutions for SAP S/4HANA
With today's challenges and economic climate, organizations leverage enterprise resource planning (ERP)...

Modern Storage The Answer to Multicloud Complexity
No matter what it's called or how it's described, it's a serious problem that's only getting worse. As...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


