Operating System

Deep Learning For Dummies
Take a deep dive into deep learning Deep learning provides the means for discerning patterns in the data...
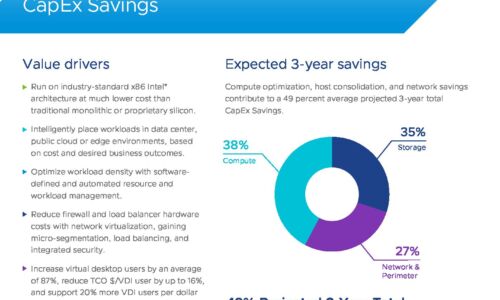
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

2022 MSP Threat Report
This report was created by the ConnectWise Cyber Research Unit (CRU)—a dedicated team of ConnectWise...

Cloud Computing for Dummies
Cloud computing is a topic that technology pros need to know to stay ahead of the computing game. Cloud...

Inside Complex Ransomware Operations and the Ransomware Economy
Ransomware operators have steadily become more sophisticated and more aligned with nation-state actors,...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...

Addressing the Top 10 Security Issues Organizations Face
Cybersecurity must be a top-level priority for any organization and for many it is. Security should be...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

Best Practices for Database Consolidation
Information Technology (IT) organizations are under pressure to manage costs, increase agility, ensure...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




