Private Networks

Security Considerations in Industrial 5G Environments
The convergence of market demand and new digital capabilities is helping companies transform their operations....

Edging Towards SASE: Next generation networking, cloud and security
The global pandemic has delivered a paradigm shift in the relationship between employees and their workplace. The...

Two-Factor Authentication Evaluation Guide
In this guide, you will learn how to evaluate a solution based on: ...

Reinventing work - New imperatives for the future of working
Following one of the most challenging years in business history, the pandemic has forced every company...

Introduction to AWS Security
Raise your security posture with AWS infrastructure and services. AWS's approach to security, including...

Getting Started with SASE
Secure Access Service Edge: A guide to secure and streamline your network infrastructure As enterprises...
Don’t Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

The State of Zero Trust Report
The zero-trust network security model has become a pervasive topic for IT professionals. Many organizations...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...
The 5G opportunity within UK industry
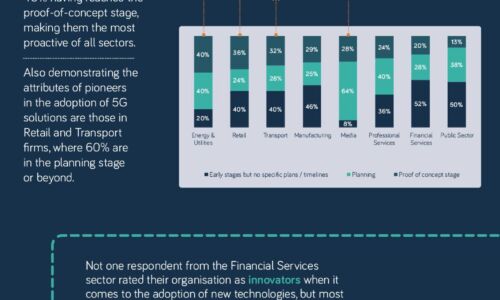
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...
What makes a 5G Leader?
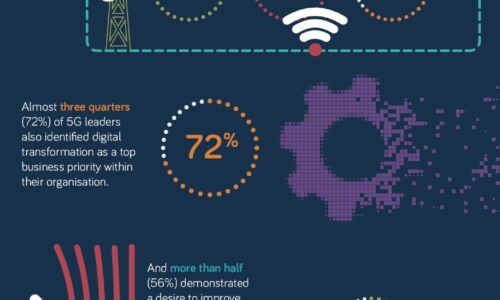
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...
- 1
- 2
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
