SaaS

AI-Driven Threat and Incident Prevention, Detection, and Response
Traditional cybersecurity, for lack of a better word, is dead. The proliferation of mobile technology...

VMware Cloud Workload Migration Tools
Before starting a cloud migration project, it is critical to understand the strategies and tools available...

Ransomware Protection Checklist
Ransomware attackers are increasingly employing more sophisticated attacks and defeating existing defenses....
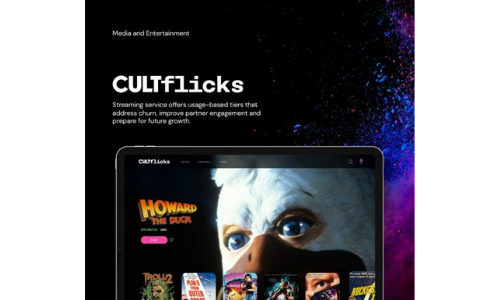
Cultflicks
CULTflicks is a niche video streaming entertainment company that offers the unique experience of specialized...

Seven Strategies to Securely Enable Remote Workers
Is your organisation ready to securely support a wide range of remote workers in the wake of a global...

Blackberry Guard: Solution Brief
While cloud and mobile technologies provide significant opportunities for digital transformation, they...

Accelerate full-stack web and mobile app development
Developing scalable, secure, high-performance web and mobile apps that empower users—while minimizing...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

Cybersecurity strategies need to evolve.
Over the past 20 years, cybersecurity strategies have primarily focused on protecting the network perimeter...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




