Security Management

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Security Strategy Checklist
This self-assessment is designed to help you evaluate the security risks in your environment. It is intended...

Illumio CloudSecure: Cloud-Native Security Simplified
Gaining unified visibility into application traffic across multi-cloud, hybrid cloud and data center...

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

Networking and Information Systems (NIS) Directive
The NIS Directive has been designed to work alongside data protection legislation. It will be governed...
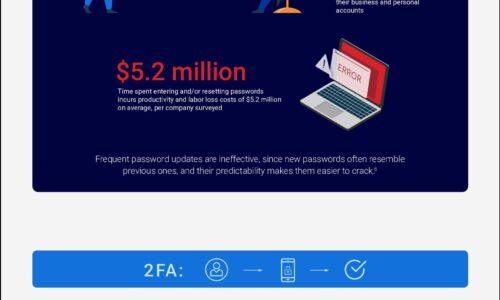
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




