Virtualization

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

SASE & ZTNA for Dummies
SASE and ZTNA combine SD-WAN efficiencies with a flexible, user-centric approach to securing remote workers...

7 Reasons VMware Cloud Foundation is the Premier Hybrid Cloud Solution
Is your IT service delivery future ready? Application and cloud strategies are inextricably linked, and...

Complete Protection at the Edge Whitepaper
How effective protection at the edge can secure the most critical assets, mitigating threats closest...

Definitive Guide to Internet Isolation
The traditional approach to cybersecurity has reached its potential, and attackers have learned how to...

Industrial IoT for Predictive Maintenance
Discover the benefits and challenges of Industrial IoT (IIoT) enabled predictive maintenance, and how...

Getting to digital experience excellence
With our Digital Acceleration program, you'll work with Adobe strategy consultants to uncover KPIs and...

2019 IT Skills and Salary Report
The 2019 IT Skills and Salary Report provides the most informative and revealing insights into the inner...
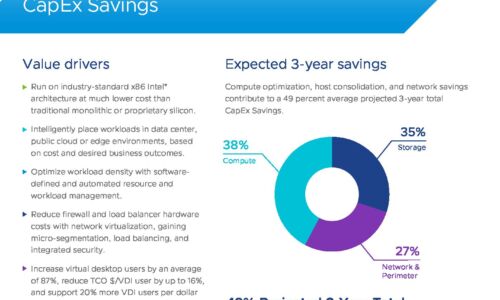
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

IoT Use Cases: Smart Ports
Smart Ports utilize Internet of Things (IoT), Artificial Intelligence (AI), and data to make itself more...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


