Applications
Ten predictions for the next decade of analytics
AI and other analytics technologies are driving incredible innovations and advancements that are making...

The confidence to carpe diem
In a world that has changed almost overnight, businesses across the planet have had to adapt just as...

Secure Access Service Edge (SASE): 7 Ways Your Business Benefits
The benefits that SASE offers organizations helps explain why Gartner estimates that by 2025, 80% of...

Advancing SOC Endpoint Incident Response Practices
Even with a comprehensive multi-layered protection solution in place, no organisation can prevent every...
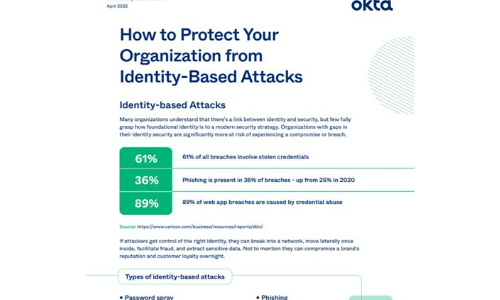
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Securing web applications in healthcare
You might think that healthcare would not be a target for criminals, but WannaCry – a strain of ransomware...

Reinvention Starts with Cloud Migration of Data Infrastructure
Take the complexity out of your data infrastructure For organizations running legacy data infrastructure...

Stay open for business — but closed to cyberthreats
E-commerce relies on always-on connectivity to customers whenever they want to access services. Your...

Forrester Consulting: Bridging The Developer and Security Divide
As security professionals work to create a secure environment for organizations, developers are often...

Building Better DDoS Mitigation
DDoS attacks have been part of the landscape for so long they can sometimes be overlooked as a threat....

Unlocking Collaboration: Making Software Work Better Together
The recent and rapid pace of change in the workplace has required companies to rethink their tools and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


