Authentication & Access Systems

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...
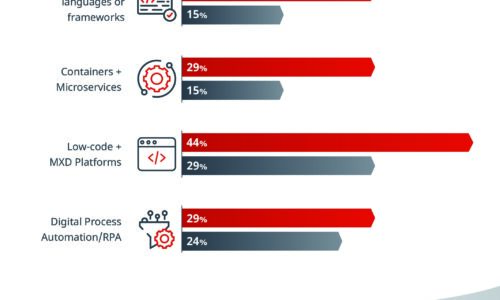
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

The Case for Secure Communications
The tapping of voice communications has occurred virtually as long as electronic communication has been...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

SD-WAN in the Age of Digital Innovation
Achieving Business Agility While Reducing Disruption. Most organisations are in the midst of some form...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

