Authentication & Access Systems

SD-WAN in the Age of Digital Innovation
Achieving Business Agility While Reducing Disruption. Most organisations are in the midst of some form...

Why automation is essential for cyber resilience
Digital transformation makes today's businesses more productive and more vulnerable to cyberattacks....
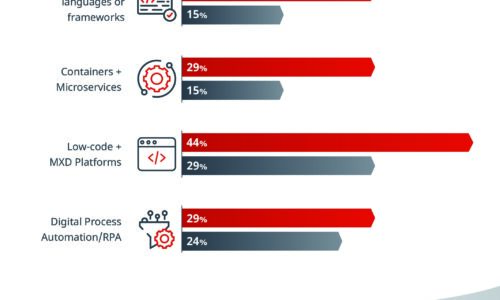
What Separates the Best from the Rest
Some IT organizations have the speed and adaptability to change course quickly when disaster strikes...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

Dissecting a Cloud Attack: Securing Azure with AzLog
Microsoft Azure is one of the fastest-growing cloud infrastructure services. Unfortunately, the advantages...

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...
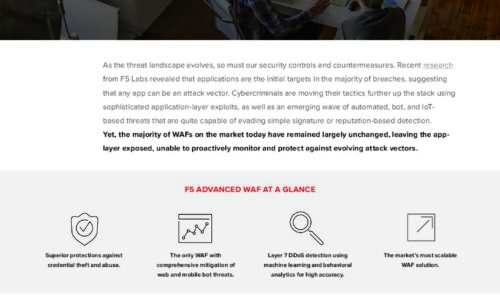
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Securing Privileged Accounts: Three Steps to Maximize Protection with MFA
Hackers are eyeing your privileged accounts, so you better be using more than 'admin123' to secure them. Multi-factor...

Understanding the Obstacles to WAN Transformation
Network engineering and operations leaders are looking to software-defined wide area networks (SD-WAN)...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

