Cloud Applications

Frost Radar™: Global SD-WAN Vendor Market,2021
Aruba earns accolades from Frost and Sullivan. Check out the Frost Radar™: Global SD-WAN Vendor Market...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Progressive CIOs: driving finance transformation
A successful finance transformation requires several ingredients: vision, agility, and the right system...

3 Benefits of Running Your Business-Critical Applications on NetApp
Make the Most of Your Essential Data Today's customers are connected. They want information at their...

The CIO’s guide to intelligent IT
Two thirds (65%) of IT decision-makers admit the conventional systems and approaches in use today aren't...

How A Hybrid Cloud Approach Supports Top IT Trends
Today's wave of digital transformation is redefining the role of the CIO, and Gartner surveys chart the...

Top 3 Security Considerations for the Cloud
Data centers are evolving to include a mix of static hardware and cloud computing technologies. However,...

5 Phases for Enterprise Migration to Amazon Web Services (AWS)
Learn about the resources, skills and processes you need to move your data to the cloud. Download now...

7 Experts on Moving to a Cloud-based Endpoint Security Platform
Without a doubt, endpoint security has become an urgent priority for many organizations, and it's not...
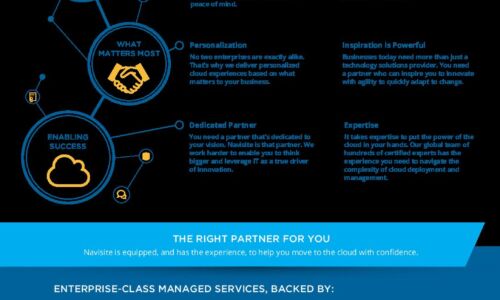
Move to the Cloud with Confidence
Navisite is a leading international provider of enterprise-class managed cloud services. But our story...

Untangling the Web of Cloud Security Threats
Changing technologies and evolving threats make IT security more challenging. Business units are adopting...

6 Ways to Deliver Business Value from your Cloud Data Warehouse
Data-driven digital transformation requires the ability to deliver trustworthy insights faster than your...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

