Connectivity

Employees are choosing how they work
'The measure of intelligence is the ability to change.' To remain connected, productive and secure in...

Accelerate ML development at scale
High-performance, low-cost machine learning for any use case Thank you for your interest. Read the eBook,...

Digital Transformation
Are organisations considering the essential foundations for digital transformation programmes to succeed? Our...

Edging Towards SASE: Next generation networking, cloud and security
The global pandemic has delivered a paradigm shift in the relationship between employees and their workplace. The...

Protecting Every Edge To Make Hackers' Jobs Harder, Not Yours
Today's users need a network that allows them to connect to any resource from any location using any...
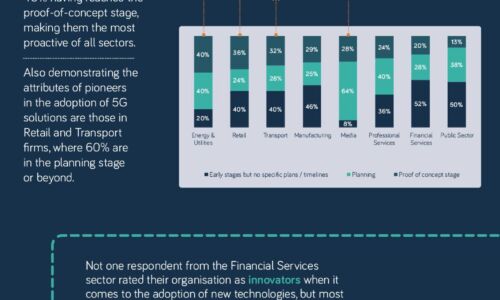
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Quest Toad for Oracle Tips and Tricks
Toad® for Oracle has been the IT community's tool of choice for more than a decade. With Toad, you are...

Digital Transformation and Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...

Responding to Crisis: A Public Sector Guide to continuity planning
Before the start of the COVID pandemic, the capabilities of cloud computing and ERP platforms were already...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




