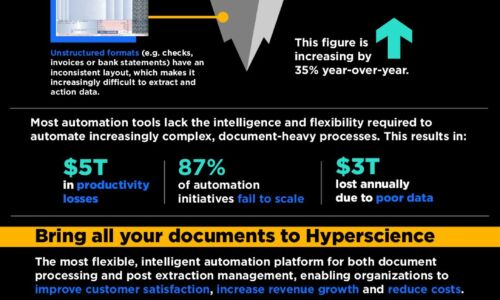
Internet of Things (IoT)

The challenges and opportunities for smart cities
With urbanisation continuing at breakneck speed around the world, governments need solutions to make...
Zero Trust: The perfect solution for the perfect security storm
We're experiencing a classic example of the perfect storm. Never have organizations faced so many challenges...

Blurred Lines and Blind Spots Report
Of the many effects the COVID-19 pandemic has had on business, one of the most dramatic has been the...

5G for the enterprise
With a desire to better understand the current, on-the-ground reality for enterprises and organisations...

Transform your business with machine learning
8 stories of machine learning success By providing the broadest and most complete set of machine learning...

Deploying Flexible Data Protection to Support Cloud Workload Placement
Digital transformation (DX) projects are designed to help organizations better utilize data for competitive...

Securing high tech industry network data
We all understand the negative impact of data loss, so why is it that so many organisations seem to be...

How to Tackle Ransomware by Managing Human Risk
CybSafe's analysis of ICO data finds the number of incidents of ransomware reported has doubled in a...

Empowering Medical Manufacturers to Become Leaders
Due to increasing technology and product complexity, regulatory requirements and supply chain issues,...

The Future of Government Operations Depends on Digital Transformation
New technologies can help government organizations reduce costs, improve constituent services, and quickly...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

The Gorilla Guide to Achieving IT Asset Management Success
ITAM is about knowing what you've got, where it is, who's using it and how much it costs. If you want...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.