Mobile Computing

Securing financial services network data
Financial services is one of the most tightly regulated business sectors. The FSA, the Data Protection...

Preparing for the post-pandemic workplace
As enterprises look towards the challenges of a post-pandemic world, one thing is widely acknowledged....

Omnichannel Loyalty
For as heartfelt of a topic as it is, navigating the world of loyalty technology can be a real pain....

A Buyer’s Guide to Audit Management Software
For today's internal audit teams, the audits themselves are only one part of a growing scope of responsibilities. Executives...

A Buyer’s Guide to Optimizing Remote Employees’ Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...

Designing Hyper-Aware Industrial Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...

M1 quick start guide
Apple will soon fully transition all the Macs in its lineup to the new ARM-based M1 chips and mobile...
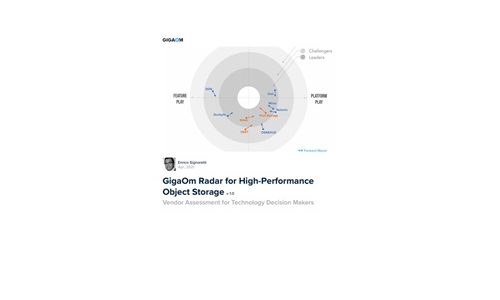
GigaOm Radar for High-Performance Object Storage
For quite some time, users have been asking for object storage solutions with better performance characteristics....

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

Securing Your 5G Edge
As service providers transition to 5G, it's important that they secure every aspect of their network....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



