Security Management

Key Steps to Optimizing Cloud Security
Do you know what's missing from your cloud security strategy? There's no question that moving to the...

An Overview of Cato Data Loss Prevention (DLP)
ata is the most valuable asset a modern enterprise has. The evolving threat landscape and shift to cloud...
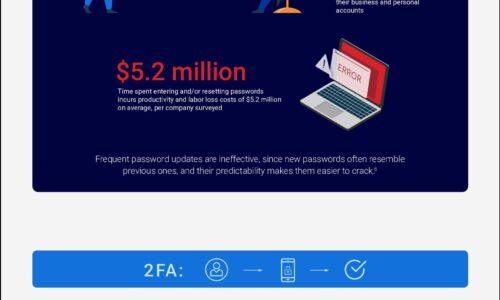
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Your Data. Their Cloud.
In today's organizations, digital transformation is a vital imperative—and cloud services offer a proven...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

5 Steps Toward Cybersecurity Resilience for Government Agencies
Cybersecurity attacks continue to grow in number, in complexity and in impact. State and local government...

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

Protecting Data Capital in your Organization
The digital era is changing the way that organizations think about, protect, and monetize data. Now more...

Automation antidotes for the top poisons in cybersecurity management
Cyberthreats are more imminent and dangerous than ever in terms of their persistence and severity. The...

How to Increase Agility with Hybrid Cloud Automation
As organizations innovate faster than ever, they bring new applications and services to market in more...

Eight Critical Practice Areas That Drive Multi-Cloud Use Maturity
While most organizations are already using two or more clouds, most teams within the larger organization...

How to secure your business with the Content Cloud
Hope is NOT a strategy: Secure your business with the Content Cloud Seems like every week there's news...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

