Security Management

Which WAF is right for me eBook
Despite the tech industry's collective best efforts to bolster secure application development practices,...

Deploying Consistent Application Services in Multi-Cloud Environments
Most organizations prioritize cloud flexibility—and let application teams choose the best environment...
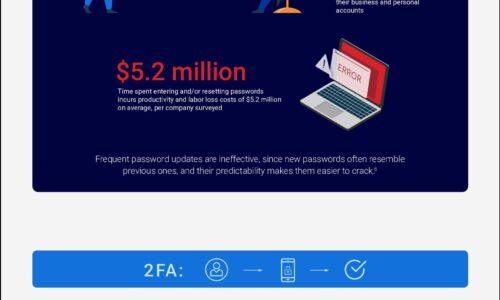
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...
Responding Smarter, Faster and Better
In cybersecurity, a critical event is a major incident that's disruptive enough to pose a meaningful...

How to secure your business with the Content Cloud
Hope is NOT a strategy: Secure your business with the Content Cloud Seems like every week there's news...

Shift your Web Security to the Cloud, for the Cloud
As enterprises embrace digital transformation, the adoption of software-as-a-service (SaaS) is robust...

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

