Server

How To Stop Lateral Attacks With Workload Microsegmentation
Network segmentation is a widely accepted tool for improving performance and boosting security. By splitting...

Splunk Predictions 2020
The future is data. In a rapidly digitizing world, data is at the root of every opportunity, and essential...

Key Storage Considerations in Determining Optimal Workload Placement
In early 2020, IDC performed in-depth primary research on how organizations determine workload placement...

Enable End-to-End Zero Trust To Achieve Effective Outcomes
Zero Trust priorities have evolved in 2020 to require solutions that secure your remote workforce with...

Debunking the Top 5 Myths About Malicious Bots
Today, as much as 40% of all Internet traffic consists of bots: non-human users that perform automated...

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...
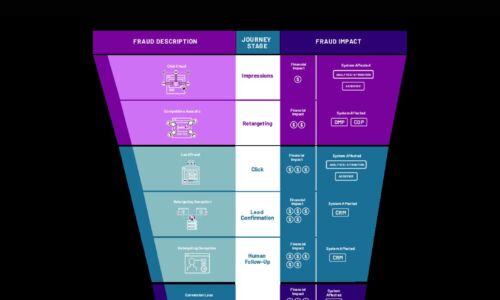
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

How Virtual Desktop Infrastructure Enables Digital Transformation
Virtual desktop infrastructure (VDI) is a foundational technology that many organizations leverage as...

VMware Cloud on AWS
Cloud infrastructure is becoming the primary deployment environment for a majority of workloads. As organizations...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




