Software

The Future of Retail is Conversations
Retail may never be the same. Consumers who were previously averse to online shopping suddenly embraced...

5G Is Changing the Game - Right Now. Is Your Infrastructure Ready?
Advanced 5G use cases will require a fundamental change in infrastructure before they can scale. As network...

Accelerate Enterprise Cloud Transformation
Accelerate Enterprise Cloud Transformation Staying competitive in today's rapidly changing marketplace...

Leading Mortgage Financier Secures Move to the Cloud With Illumio
As a top lender focused on getting people into homes and keeping ransomware out of its IT environments,...

Building Your Best Boardroom
How to Find the Right Directors For a Complex Future With the advent of modern governance, directors...

Where you need trust, you need PKI
On a rainy summer day in 2013, a small, float-equipped plane stalled while flying low over the mountains...

10 Biggest and boldest insider threats
Over the last two years alone, insider security incidents have jumped 47%, with the average cost per...

Fortinet Secures the Intelligent Enterprise Running SAP
Business leaders embrace SAP HANA functionality to stay on top of emerging trends and evolving business...

Inside The Mind of a Hacker 2019
The first step in cybersecurity? Think like a hacker. According to a recent report, 71% of cybercriminals...
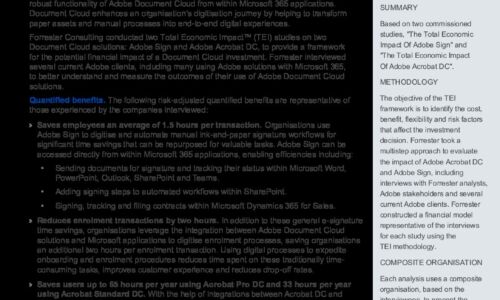
The Total Economic Impact of Adobe Document Cloud & Microsoft Spotlight
Forrester interviewed several current Adobe clients, including many using Adobe solutions with Microsoft...

The 7 Hidden Truths of Cloud Security
Based on extensive, up-to-date knowledge and experience from WithSecure consultants, threat hunters and...

Five Best Practices for Mitigating DDoS Attacks
Distributed denial-of-service (DDoS) attacks remain one of the most effective methods used by cybercriminals...

The Ponemon 2021 Cost of Phishing Study
The financial effects of phishing attacks have soared as organisations shift to remote and hybrid work....

An Authentication Authority at Your Fingertips: PingFederate
Having an authentication authority within your infrastructure allows you to have a single source of truth...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.